SafeLine offers three distinct performance modes to meet different system requirements and traffic loads. Each mode is designed to provide an optimal balance between resource consumption and request handling capacity.
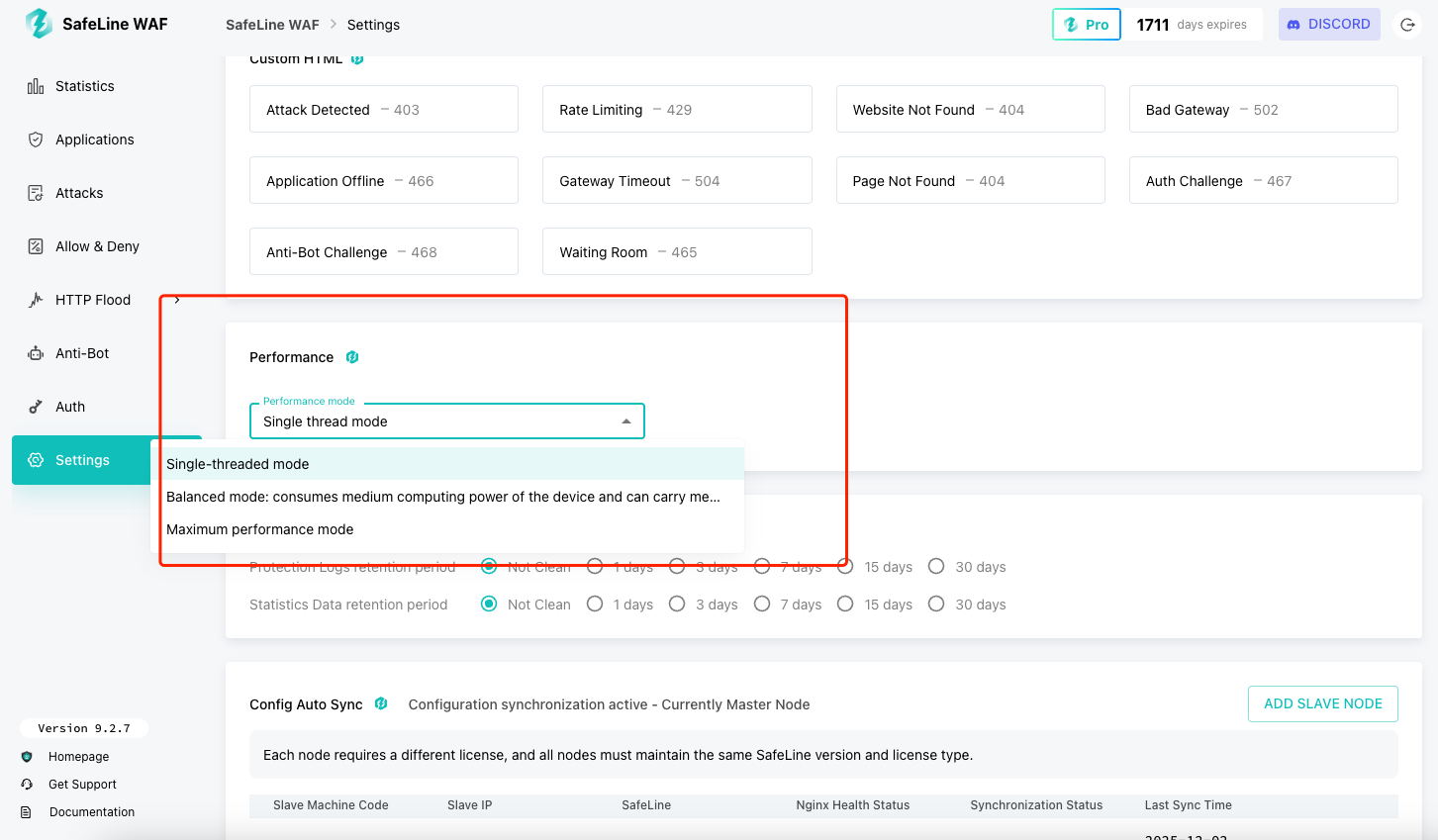
1. Single-threaded Mode
- Default performance setting
- Minimal resource consumption on your device
- Recommended for environments with limited computing resources
- Suitable for low-traffic websites and testing environments
- Prioritizes efficiency over high throughput
2. Balanced Mode
- Moderate resource utilization
- Medium QPS (Queries Per Second) capacity
- Ideal for standard production environments
- Provides a good compromise between performance and resource efficiency
- Recommended for most general use cases
3. Maximum Performance Mode
- Highest resource utilization
- Maximum QPS handling capability
- Designed for high-traffic websites and critical applications
- Optimized for environments where performance is the top priority
- Requires more robust hardware specifications
By selecting the appropriate performance mode, users can tailor SafeLine to their specific infrastructure, ensuring optimal protection and efficiency for their websites or applications.
Resources
SafeLine Website: https://ly.safepoint.cloud/ShZAy9x
Live Demo: https://demo.waf.chaitin.com:9443/statistics
Discord: https://discord.gg/dy3JT7dkmY
Doc: https://docs.waf.chaitin.com/en/home
Github: https://github.com/chaitin/SafeLine