A couple of months ago, I came across a WordPress site that needed a quick security check for obvious vulnerabilities. It all started with routine work: standard checks, searching for known CVEs, and inspecting popular plugins. But what I found made me think more seriously — critical Arbitrary File Download vulnerabilities in several plugins that allowed access to wp-config.php with just a few requests
This became the reason for creating CR4SH3R — a simple yet powerful tool designed to automate the detection of such vulnerabilities within the WordPress ecosystem
What is it?
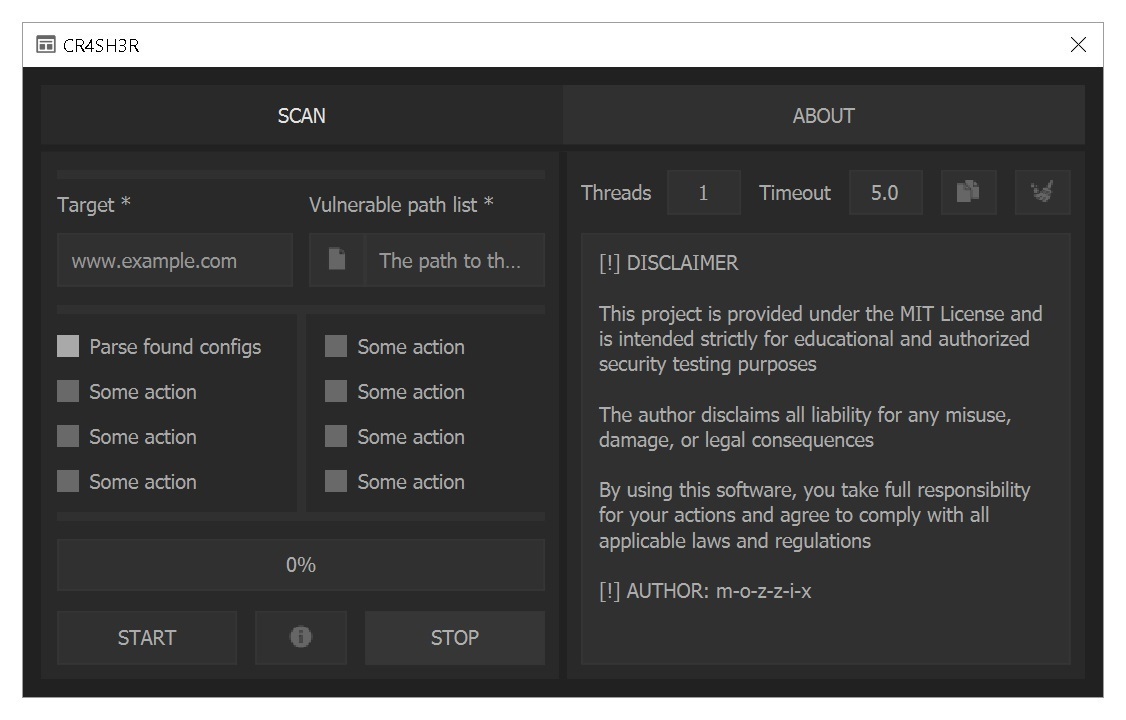
CR4SH3R is a GUI utility designed to scan websites for Arbitrary File Download vulnerabilities in WordPress plugins. Its main purpose is to detect paths through which the wp-config.php file can be downloaded, and automatically extract sensitive information from it — such as database login credentials and other important parameters
Screenshots
How does it work?
The scanner uses a pre-prepared list of potentially vulnerable URL paths and sends HTTP requests to the target domain. If the server returns the contents of the wp-config.php file, the program parses it and displays only the relevant data. There’s also an option to save results in .xlsx format
Example payload:
/wp-content/plugins/vulnerable-plugin/download.php?file=../../../../wp-config.php
Key Features:
Multi-threaded Scanning
Fast scanning using concurrent request processing. Supports up to 10 simultaneous checks
Automatic Data Extraction from wp-config.php
If the file is found, CR4SH3R automatically extracts values like:
DB_NAME
DB_USER
DB_PASSWORD
DB_HOST
table_prefix
Excel (.xlsx) Report Generation
All findings are saved in a structured and easy-to-share format
Simple GUI Interface
Built using PyQt5 for user-friendly interaction
Roadmap:
Auto-updater — built-in version checker
Config Presets — save and load frequently used scan settings
Session History — track previous scans with timestamps and results
Encrypted .env File — prevent plaintext exposure when bundled into binaries
Repository Link
https://github.com/m-o-z-z-i-x/CR4SH3R