PassForge Pro is a cutting-edge, zero-knowledge, local-first password vault designed with advanced security measures to ensure the highest level of digital privacy. This application leverages AES-256 encryption for safeguarding credentials stored within an SQLite database that exists solely on the user's machine, thereby avoiding cloud dependency and telemetry.
Key Features
PassForge Pro functions as a cryptographic fortress, meticulously crafted for security professionals and individuals who prioritize absolute digital sovereignty. The following core features highlight its robust design:
- Zero-Knowledge Architecture: Master passwords never leave RAM, ensuring that user data remains inaccessible to anyone, including the developers.
- Local-First Approach: Without cloud synchronization or network connections, the vault remains entirely within the user's control.
- Memory Safety: All sensitive data is purged from RAM immediately after use to prevent recovery.
- Open Source: The entire codebase is available for auditing and improvement by the community.
️ Advanced Security Protocols
The application employs a suite of sophisticated security protocols, including:
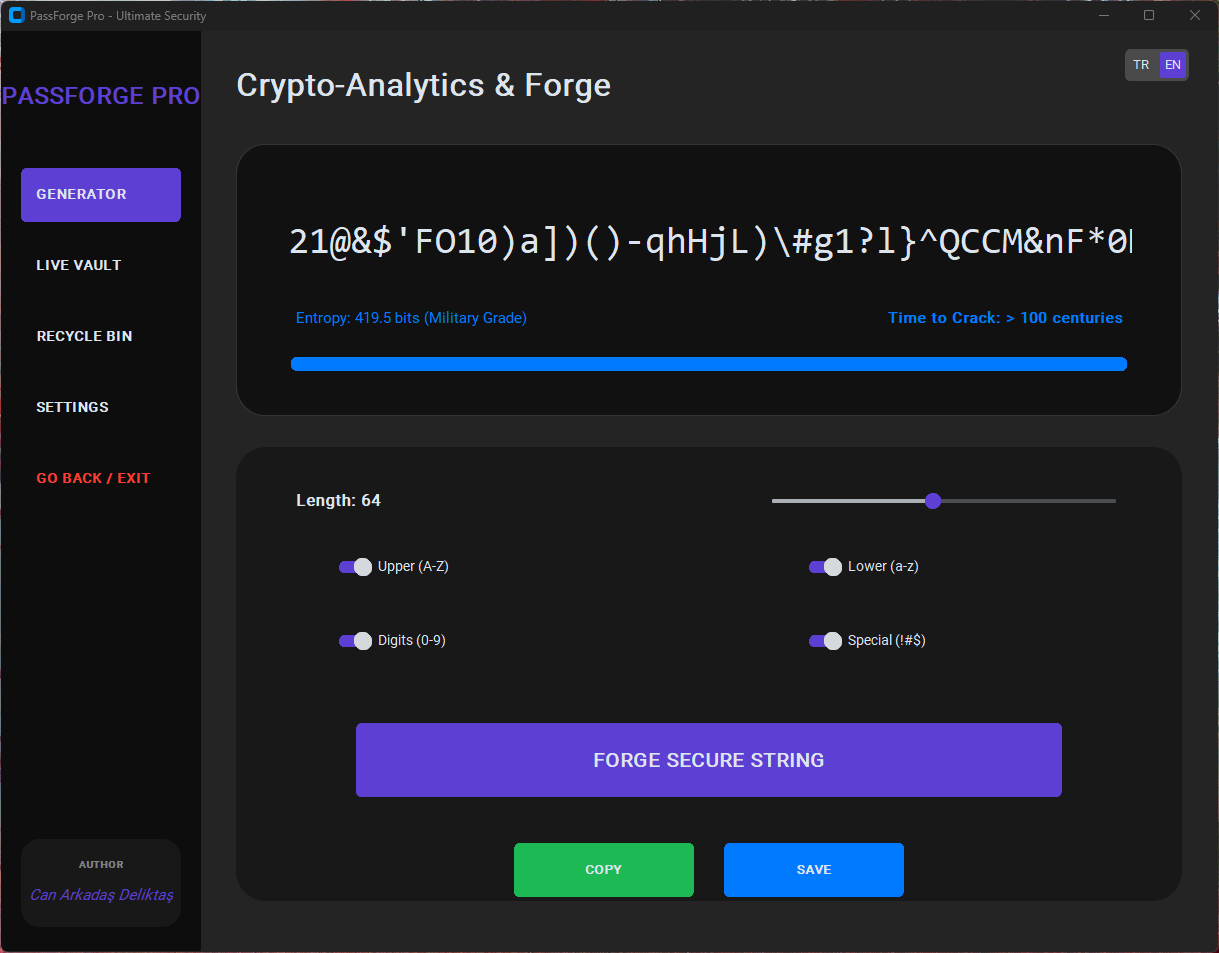
- Military-Grade Encryption: Utilizes AES-256 GCM and Fernet authenticated encryption for optimal data protection.
- Adaptive Key Derivation: Implements PBKDF2-HMAC-SHA256 with 150,000 iterations alongside BCrypt for enhanced security.
- Ghost Protocol: Employs signature masking in system directories to mitigate risks associated with static analysis.
- Noisy Wipe: Incorporates multi-pass recursive sector overwriting to securely delete sensitive data.
- Autonomous Locking: Features inactivity-based memory purging and automatic vault closure to fortify security.
- Clipboard Sanitation: Automatically wipes sensitive data from the OS clipboard to prevent unintended exposure.
✨ Functional Highlights
| Feature | Description |
|---|
| AES-256 GCM Encryption | Military-standard authenticated encryption. |
| PBKDF2-HMAC-SHA256 | Over 150,000 iterations for key derivation. |
| Memory Purging | Immediate RAM wipes upon locking, exiting, or after inactivity. |
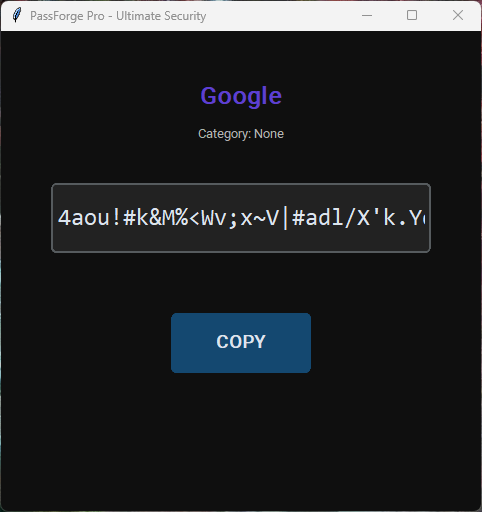
| Clipboard Sanitization | Automated clearing after a specified delay. |
| ⏱️ Auto-Lock Timer | User-configurable inactivity timeout for added security. |
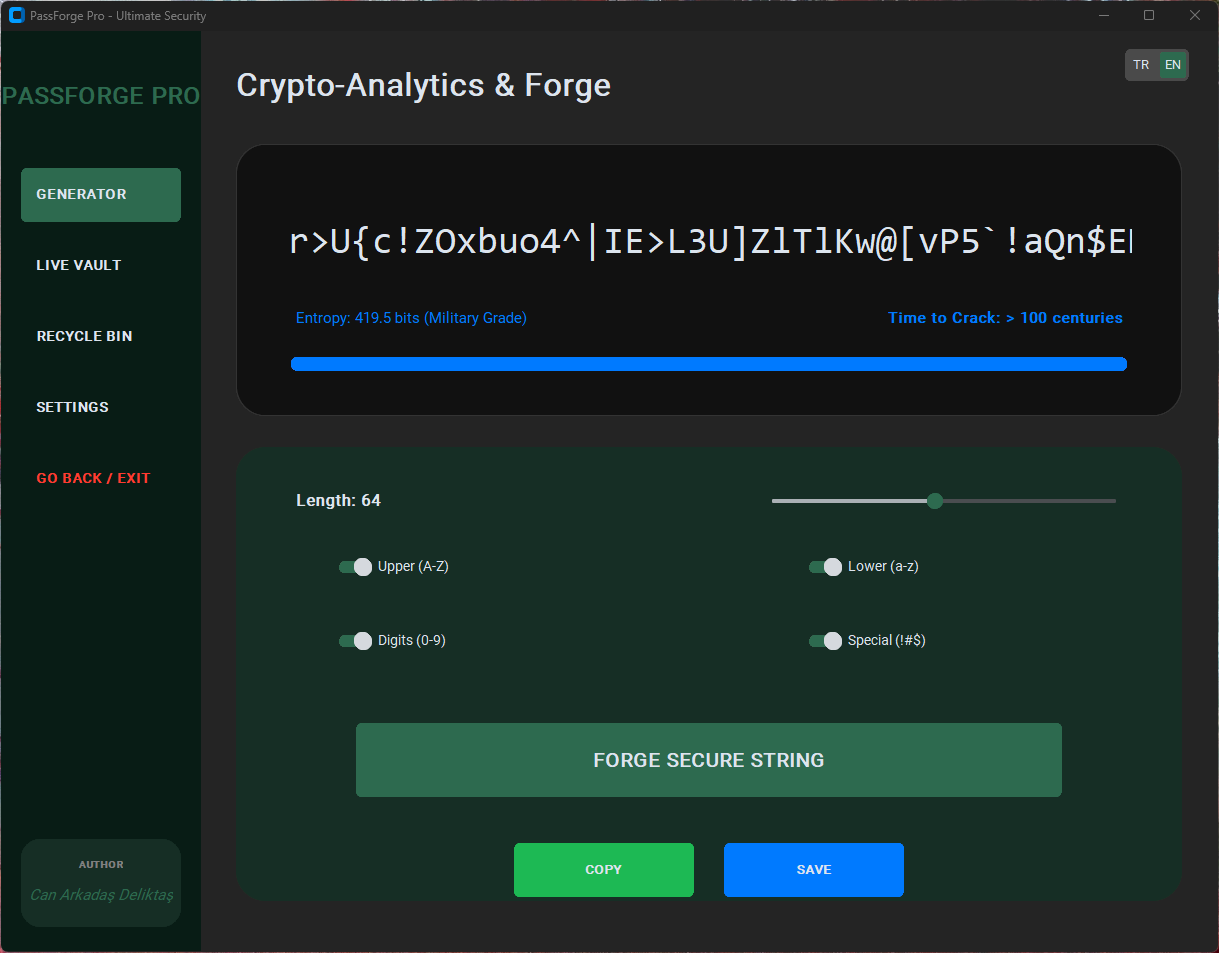
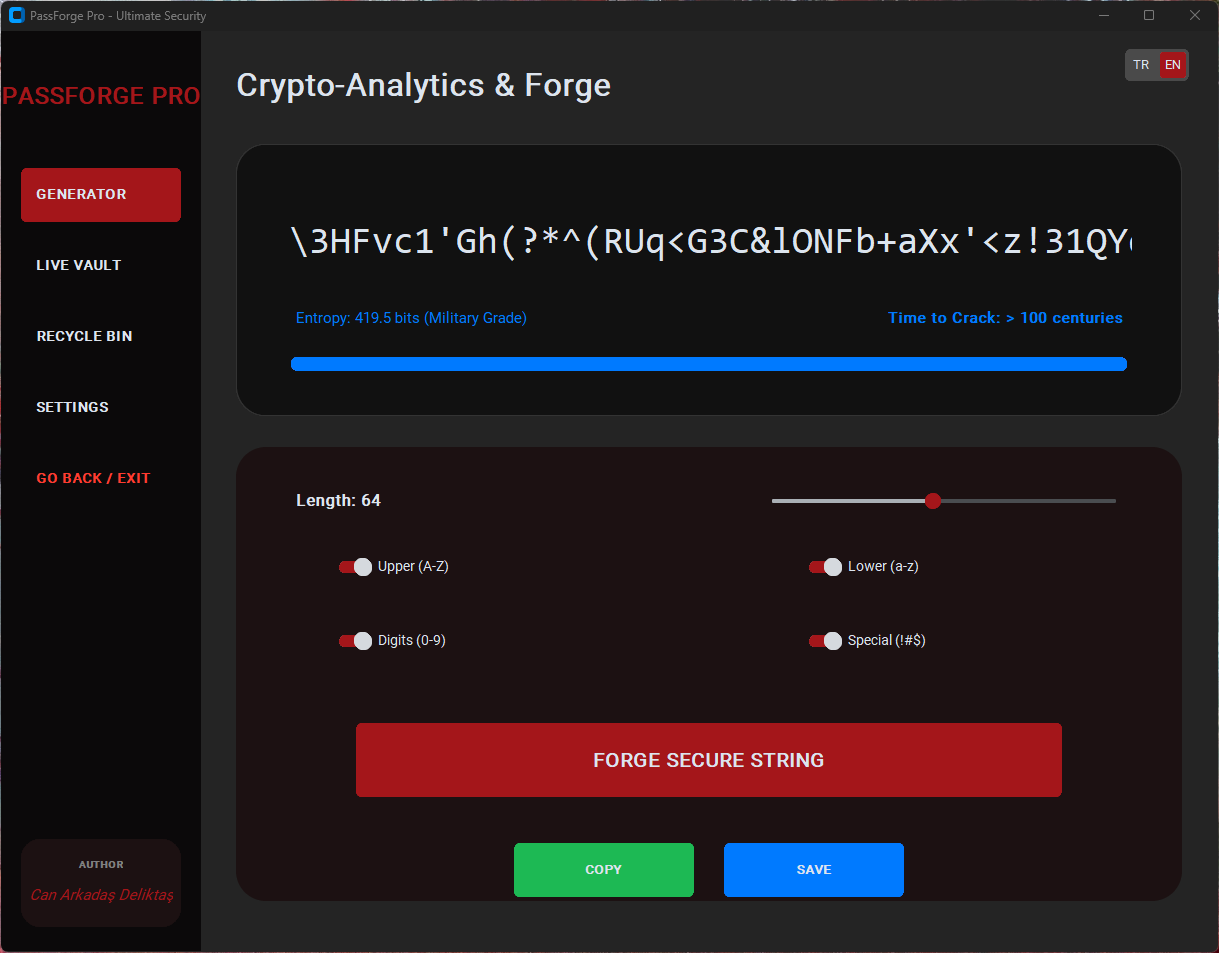
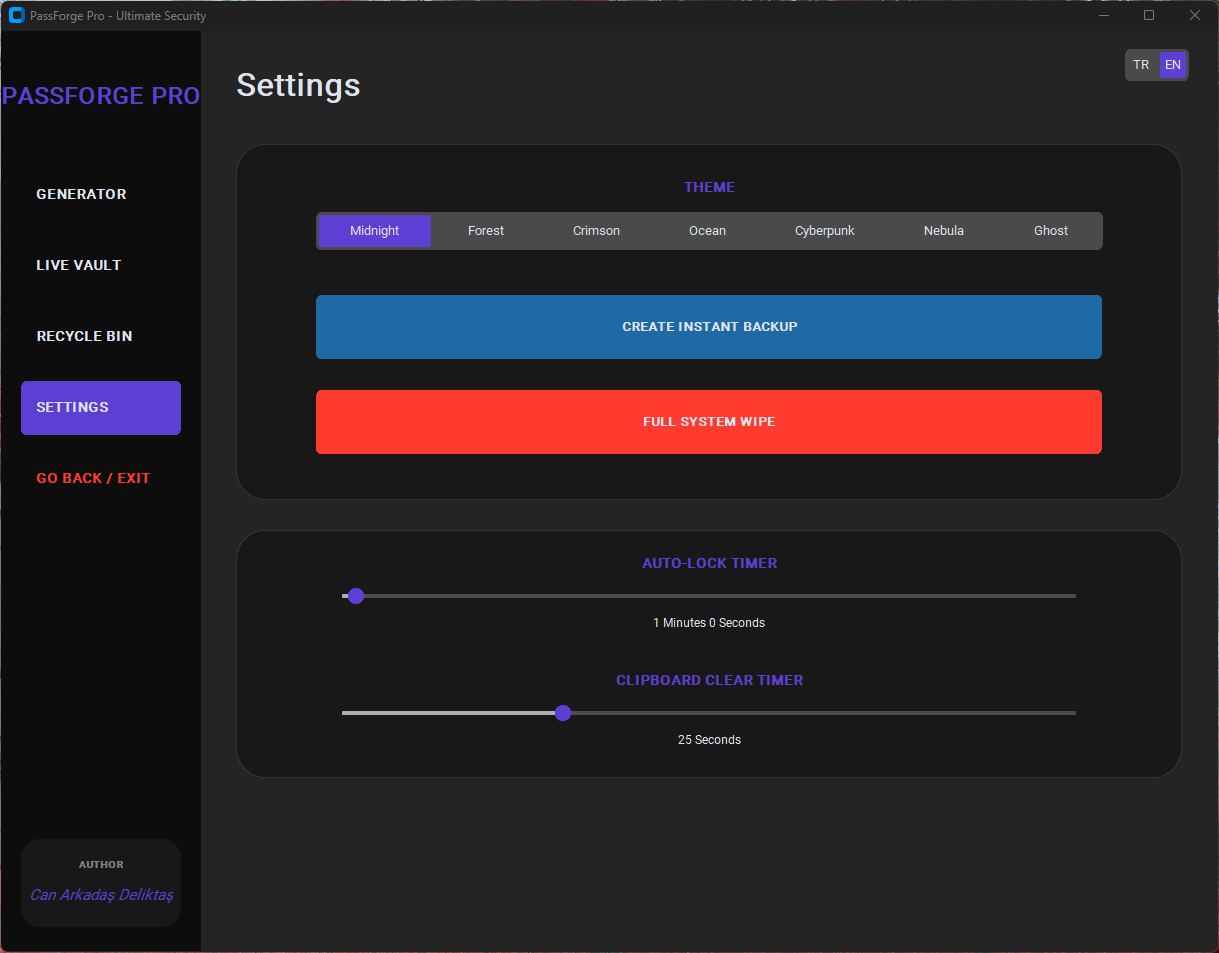
| 7 Premium Themes | Choose from several visually engaging themes, including Cyberpunk and Neon. |
| Folder Hierarchy | Enables unlimited nested categories for organized credential storage. |
| Trash Recovery | Provides a soft delete feature for up to 30 days before permanent removal. |
| Password Generator | Generates secure, random passwords based on user-defined rules. |
⚠️ Important Considerations
Using PassForge Pro involves a legal disclaimer:
- Users accept full responsibility for their data security and management.
- Users must ensure compliance with local laws regarding digital privacy and encryption.
- There is no recovery mechanism for lost master passwords, leading to potential irreversible data loss.
For a thorough understanding of usage and compliance, refer to the Privacy & Security Policy.
PassForgePro: Learning-focused Local-Only Password Manager
Hi fellow developers, open-source enthusiasts, and security fans!
I’m excited to share PassForgePro, a personal project I built to explore the design, security, and practical challenges of local-only password managers.
⚠️ Disclaimer: This project is experimental and unaudited. It is not intended to replace mature tools like Bitwarden, KeePass, or 1Password. Use it only for learning, testing, or feedback.
Key Goals
- Learning: Understand practical password manager challenges
- Cryptography: AES-256-GCM encryption, PBKDF2 key derivation
- Privacy: Local-only, zero-knowledge vaults
- Security: Threat modeling, memory & clipboard hygiene
- Feedback: Community input for improvement
Features & Screenshots
Login & Authentication
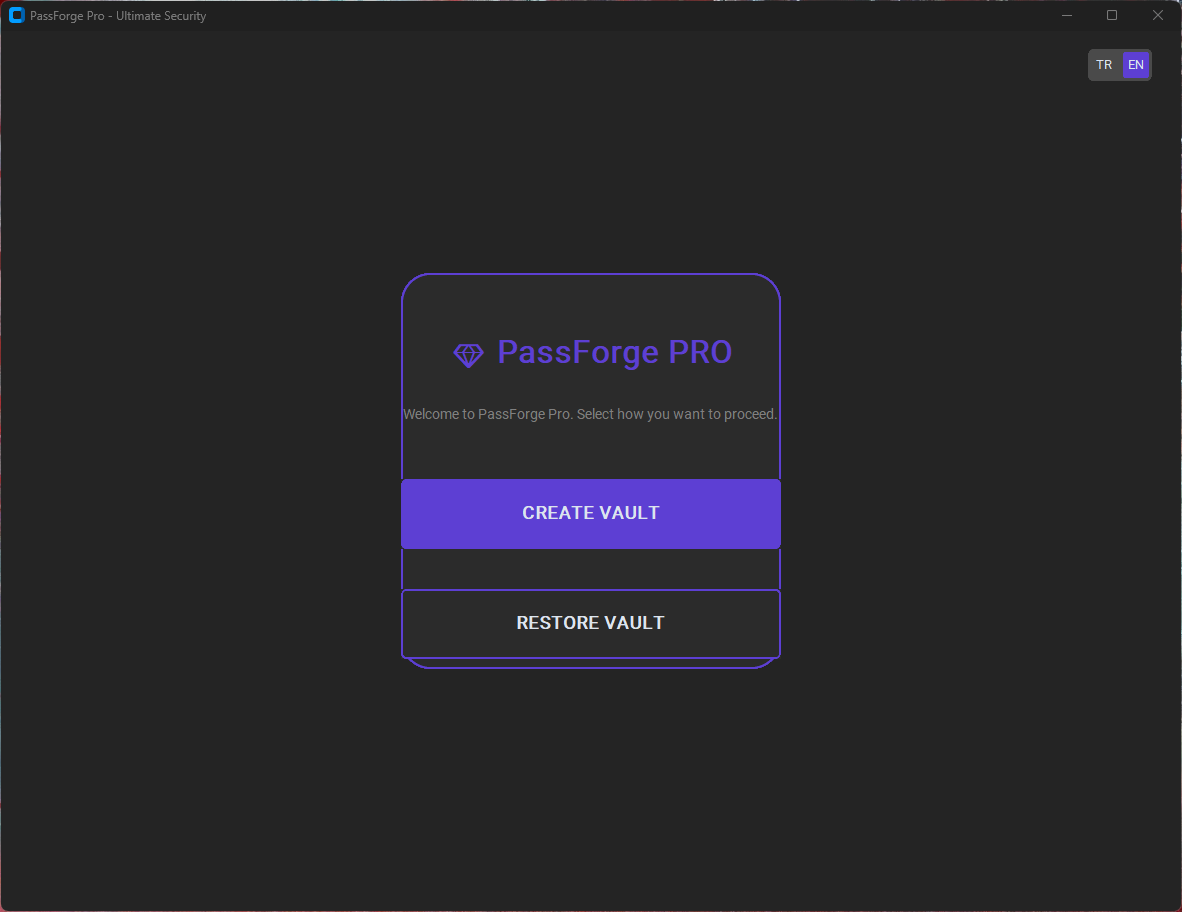
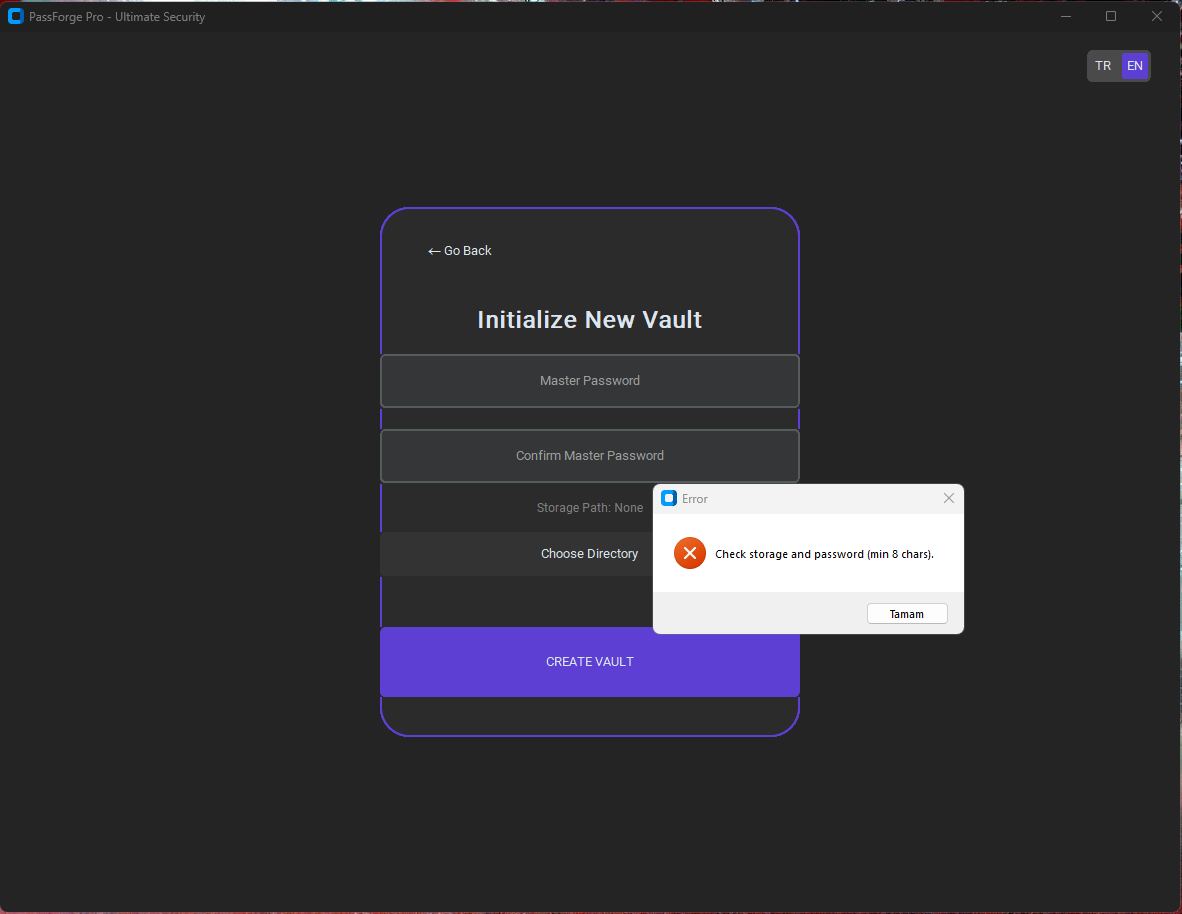
Vault Management
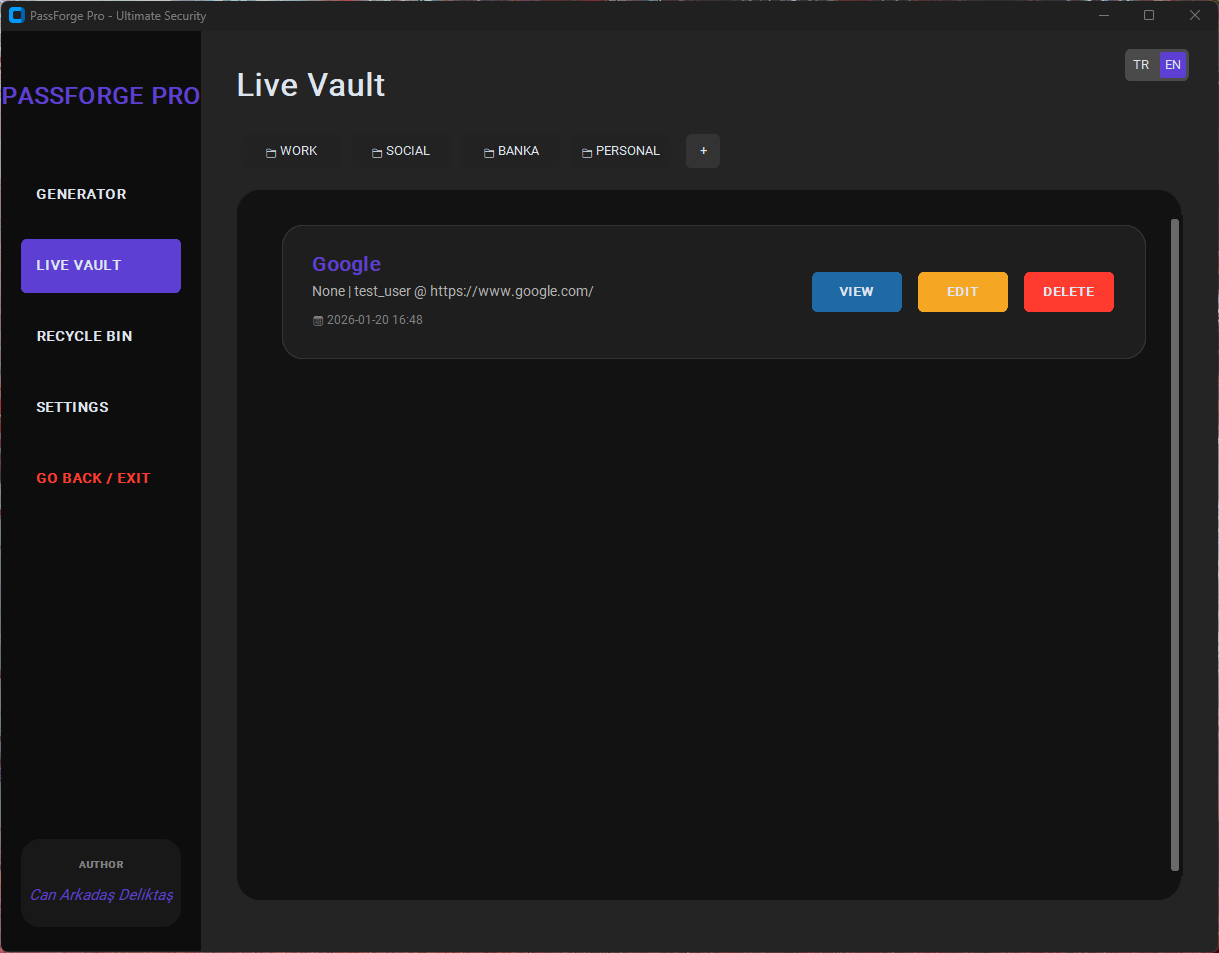
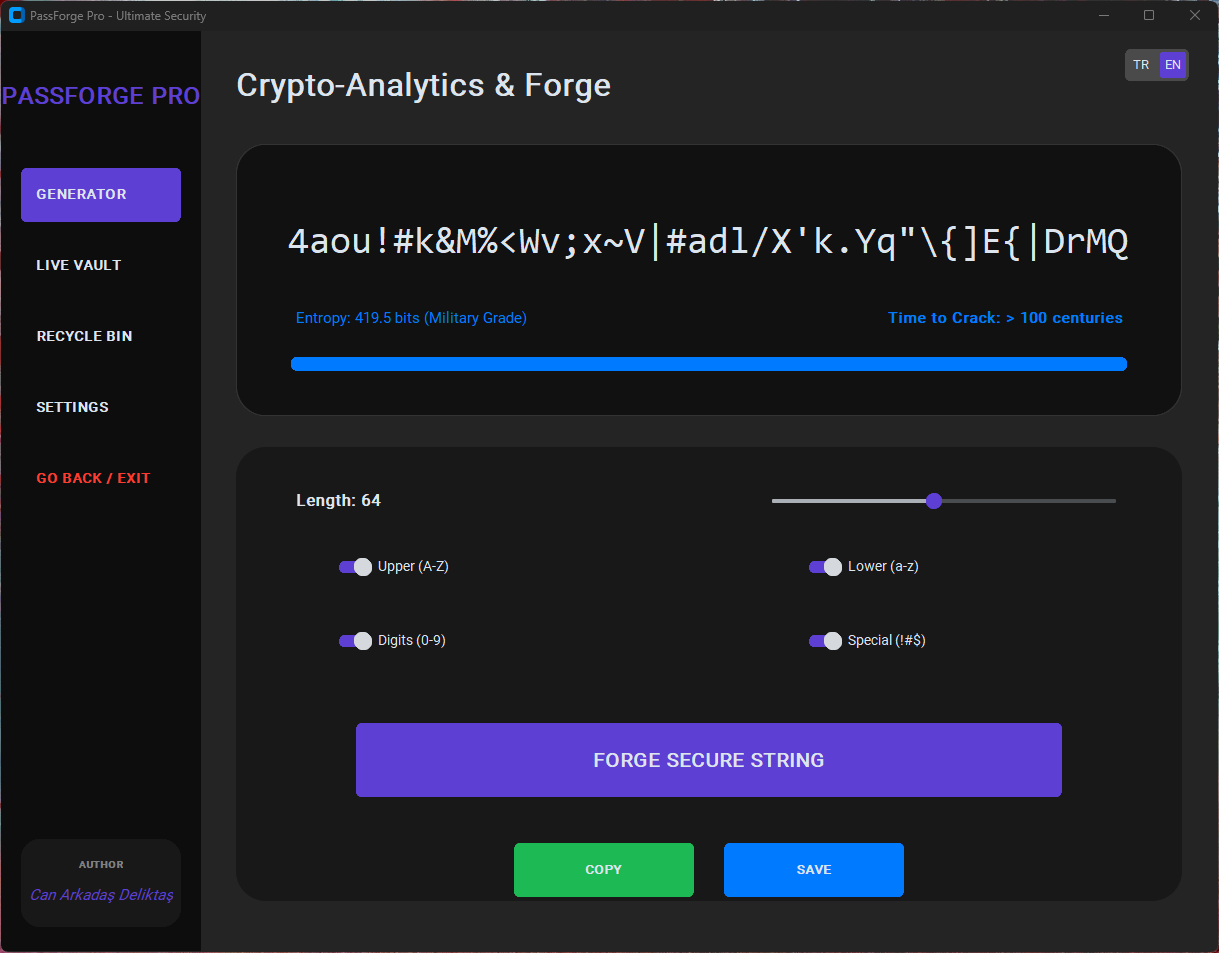
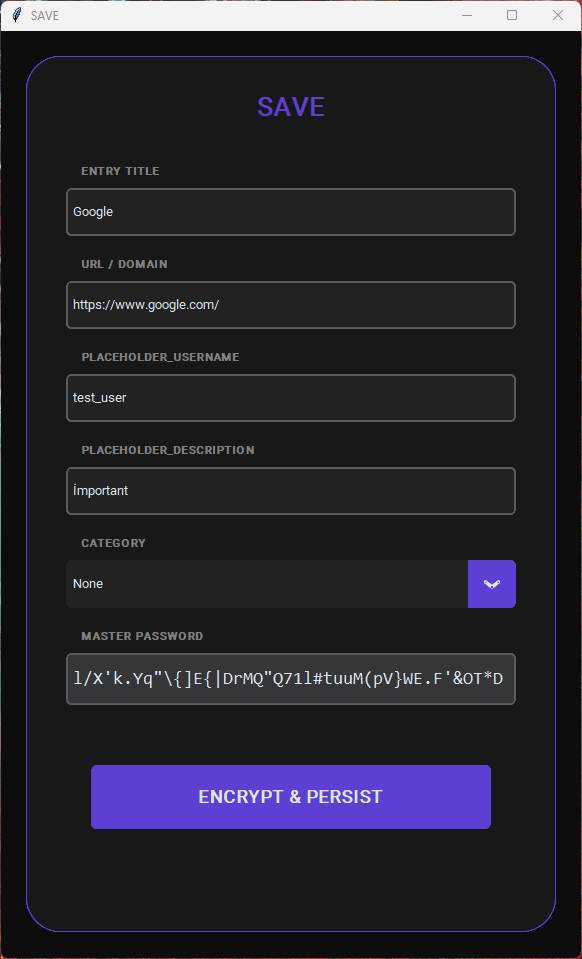
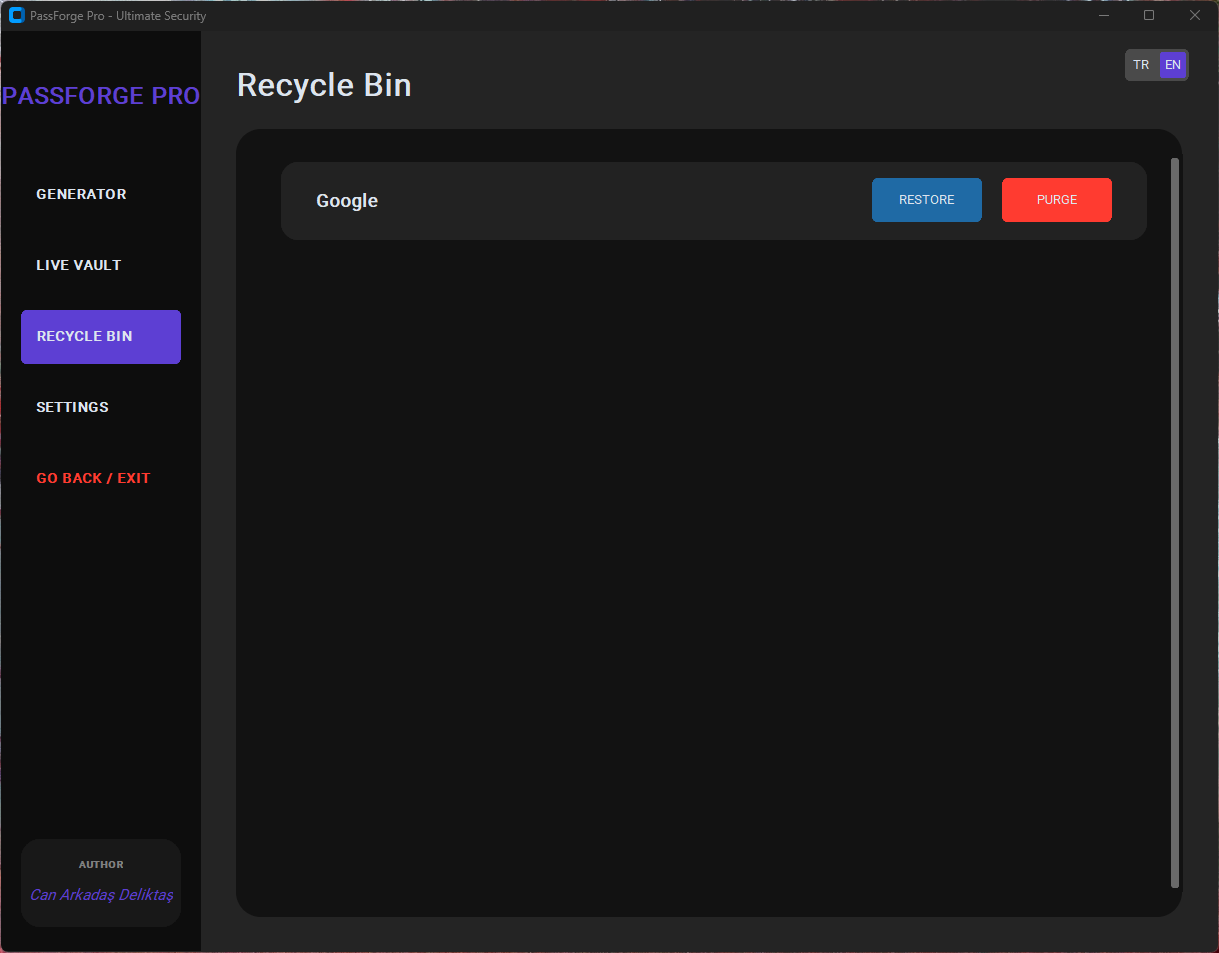
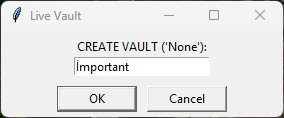
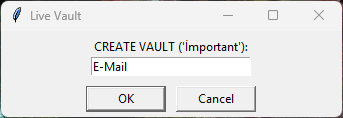
Folder & Subfolder Handling
Copying & Themes
Links
What I’m looking for
I’d really appreciate feedback from developers and security enthusiasts on:
- Architecture and code design
- Cryptography choices
- Threat modeling and limitations
Any suggestions, critiques, or collaboration ideas are highly welcome!
TL;DR
- Learning-focused local-only password manager
- AES-256-GCM encryption + PBKDF2
- Experimental, unaudited
- Open to community feedback